It is no longer news that the malware more popularly referred to by experts as WannaCry (or WannaCrypt, WanaCrypt0r 2.0, Wanna Decryptor) is a ransomware program targeting Microsoft Windows operating systems worldwide. Why is it called a ransomware? it is so-called because on Friday, 12 May 2017, a large cyber-attack using this malware was launched, infecting more than 230,000 computers in 150 countries, and demanding ransom payments in the cryptocurrency bitcoin in 28 languages (see image below).
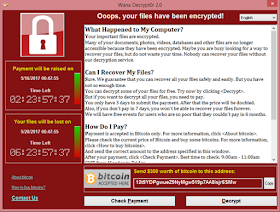 |
| Screenshot of a ransom note left on an infected system: The malware demands ransom payments from victims in the cryptocurrency bitcoin in 28 languages, thus the name, ransomware |
Several hours after the initial release of the ransomware, MalwareTech accidentally discovered what amounted to be a "kill switch" hardcoded in the malware while he was trying to establish the size of the attack. Registering a domain name for a DNS sinkhole stopped the attack spreading as a worm. While this did not help already infected systems, it slowed the spread of the initial infection and gave time for defensive measures to be deployed worldwide, particularly in North America and Asia, which had not been attacked to the same extent as elsewhere.
How to protect yourself
The more important question now is, "How do you protect yourself from the rampaging attack of this malware?" While Microsoft, in an unusual move, has created security patches for several now-unsupported versions of Windows, including Windows XP, Windows 8 and Windows Server 2003; there are still some seemingly simple steps you can and should take which would help protect you the more and keep your systems safe.First of all, you must realise that these attacks are spread by multiple methods, including phishing emails and on unpatched systems as a computer worm. Thus, a proactive defense strategy which builds common sense into all you do online must be the common denominational factor. Making computer treatment choices after an attack can be very difficult and costly. Proactive defense is key to mitigating operational risk.
1). Your emails.
The key here is to be wary of your emails. You must be vigilant when opening emails. If you have any suspicious looking email message, it is always better to err on the side of caution than to regret later. From the experiences of those who were recently affected, I have drawn up this short common sense advise on using your email:- You must be vigilant when opening your emails. Be sure you recognise the sender's address, or at least, it makes sense to you. Look at sender's address or name before opening.
- Specifically, if you have the following attachment on any email you must not open it:
Ransom note name: @Please_Read_Me@.txt
- Delete the email from your in-box.
Also go to your deleted items and delete it from there too. - If it accidentally activates by any means and the above screenshot is displayed, immediately turn off your computer, and remove the network cable from its socket (if you're using a wire cable).
- Contact IT Security immediately. If you know none, see number 4 below.
2). Backups and security patches.
Another issue to look at is backups and security patches. In this attack, the dramatic demonstration of the value of having good, secure backups and good cyber-security including having the latest security patches installed have been forcefully demonstrated. These do not need much elaborating on.Again, however, I hail Microsoft because by releasing an out of bounds patch for unsupported operating systems such as Windows XP and Server 2003, people now are able to patch rather than having to attempt upgrades to newer operating systems in order to be secured against this worm. If you have anything to patch, patch it. If you need a guide, this one is being regularly updated: https://www.ncsc.gov.uk/guidance/protecting-your-organisation-ransomware.
3). Maintain good Cyber hygiene.
Wikipedia defines this so: "Cyber hygiene is the establishment and maintenance of an individual's online safety. It is the online analogue of personal hygiene, and encapsulates the daily routines, occasional checks and general behaviours required to maintain a user's online "health" (security)."There is so much to understand from that simple definition. In a nutshell, it says we should all have good cyber-hygiene, which in essence, is the summary of what we've discussed in 1 and 2 above, and more like refraining from clicking on links you don't understand (may end up being phishing links), be careful which emails you open, ensure to back up your data properly and securely, and generally employing common sense in all you do online. Always bear in mind, as noted by James Scott from the Institute of Critical Infrastructure Technology, that "you're only as strong as your weakest link within your organisation from a cyber-perspective".
4). Computer Security Incident Response Team, CSIRT
Finally, if you do fall a victim, advertently or inadvertently, there's the Computer Security Incident Response Team, CSIRT. This would actually depend on the country you live in, as not all countries have the CSIRT; and among those who do, not all CSIRT may respond to non-government individual citizen calls and queries. However, it is useful to know about them and how your country uses them.I will try to make a post summarizing the CSIRTs available in different parts and countries of the world, and what their roles are to citizens in those countries. Until then, however, if you do fall victim to this ransomware, you may want to see if you can reach out to the CSIRT overseeing your region here or your country here (links opens in a new window).
Related: Recent articles on internet and computer security

No comments:
Post a Comment